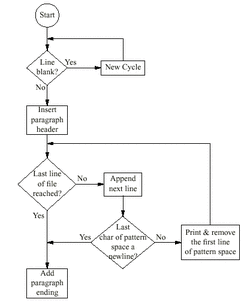
A flowchart is a type of diagram that represents an algorithm or process, showing the steps as boxes of various kinds, and their order by connecting them with arrows. Process operations are represented in these boxes. Rather, they are implied by the sequencing of operations. Flowcharts are used in analyzing, designing, documenting or managing a process or program in various fields.
Flowcharts can be modeled from the perspective of different user groups (such as managers, system analysts and clerks) and that there are four general types.
Document flowcharts, showing controls over a document-flow through a system
Data flowcharts, showing controls over a data-flow in a system
System flowcharts showing controls at a physical or resource level
Program flowchart, showing the controls in a program within a system
For a computer engineering, for example, he may need to draw a program flowchart before creating new software. They can also use tools like Athtek Flowchart to code which can directly convert the flowchart they designed to code.
More recently Mark A. Fryman (2001) stated that there are more differences: "Decision flowcharts, logic flowcharts, systems flowcharts, product flowcharts, and process flowcharts are just a few of the different types of flowcharts that are used in business and government".
In addition, many diagram techniques exist that are similar to flowcharts but carry a different name, such as UML activity diagrams.

 RSS Feed
RSS Feed